Industry’s best catch rate of known and zero-day malware
A recognized Industry Leader as seen in AV-TEST Corporate Endpoint Protection and NSS Advanced Endpoint Protection lab tests of 2020, Harmony Endpoint is powered by over 60 threat prevention engines and fueled by Check Point ThreatCloud™, the world’s most powerful threat intelligence to deliver the highest overall threat catch rate in the market.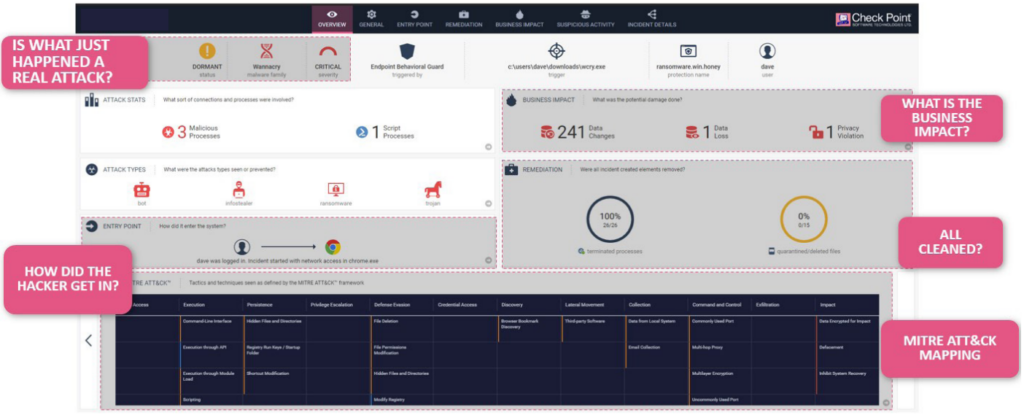
Flexibility
The Check Point Harmony suite of products can be managed either on-premise or via the Check Point Infinity Portal. If you are an existing Check Point customer, you can leverage the easy setup and the advanced Threat Hunting capabilities of the Infinity Portal whilst still collecting Harmony Endpoint logs to your existing on-premise management server for full log visibility in a single location. The Harmony agent can be installed on a variety of operating systems, covering Windows, MacOS and Linux, as well as support in certain VDI infrastructures giving you complete coverage across your enterprise network. Installation can be completed manually with a small installer or can be packaged into third-party solutions such as InTune, SCCM or GPO. Updates and upgrades can be handled within the Harmony Endpoint agent itself, reducing the administrative burden.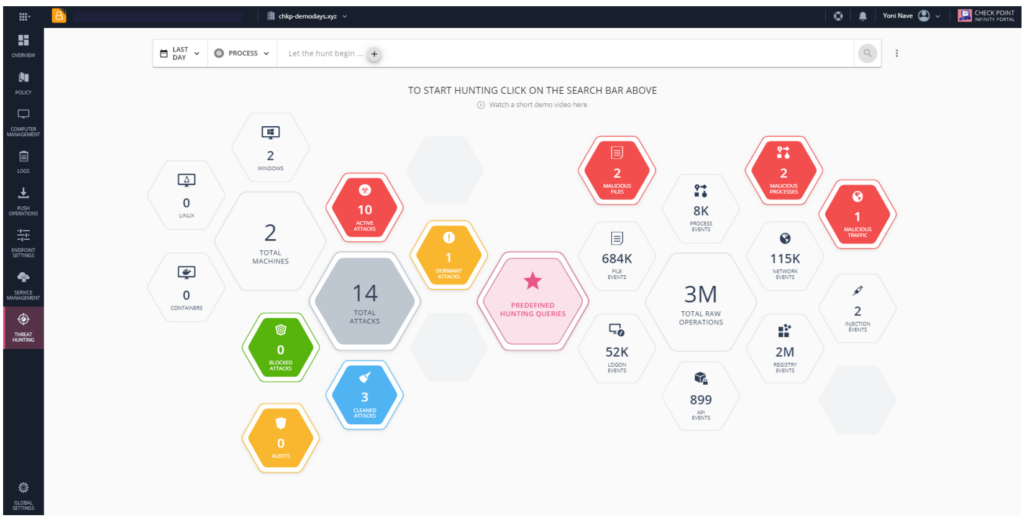
License Packages
Check Point Harmony Endpoint is available in 4 different license packages, allowing you to tailor your protection needs to your organisation.
Harmony Endpoint Data Protection
-
Full Disk Encryption
-
Removable Media Encryption
-
Access Control and Port Protection
-
Endpoint Compliance
Harmony Endpoint Basic
-
Endpoint Compliance
-
Anti-Ransomware
-
Zero-day Phishing
-
Advanced Threat Prevention
-
Endpoint Detection and Response (EDR)
-
Endpoint Compliance
Harmony Endpoint Advanced
-
Endpoint Compliance
-
Anti-Ransomware
-
Zero-day Phishing
-
Advanced Threat Prevention
-
Endpoint Detection and Response (EDR)
-
Threat Emulation
-
Threat Extraction
-
Endpoint Compliance
Harmony Endpoint Complete
-
Endpoint Compliance
-
Anti-Ransomware
-
Zero-day Phishing
-
Advanced Threat Prevention
-
Endpoint Detection and Response (EDR)
-
Threat Emulation
-
Threat Extraction
-
Data Protection (Full Disk and Media Encryption)
-
Endpoint Compliance
Check Point Harmony Endpoint – Complete
The Complete package of Check Point Harmony Endpoint combines all of the features of the suite, providing the ultimate level of security across your endpoints.
With one single, unified agent providing Endpoint Encryption and Port Protection, Endpoint Detection and Response, Next-Generation AntiVirus, VPN for remote access as well as web-browser based security, the Check Point Harmony Endpoint – Advanced package streamlines your endpoint protection and reduces your Total Cost of Ownership.
The Complete package for Check Point Harmony Endpoint provides a suite of protections for your endpoints covering all of the needs of an organisation.
To find out more about Check Point Harmony Endpoint – Complete, to set up a Proof of Concept or Trial, please contact us now.
Check Point Harmony Endpoint – Advanced
The Advanced package of Check Point Harmony Mobile brings a full suite of endpoint protection functionality and is one of the most popular package options available from Check Point.
The package contains a suite of Endpoint protection blades, including Next-Generation Anti Virus, Anti-Ransomeware, Remote Access VPN as well as the Threat Emulation and Threat Extraction technologies.
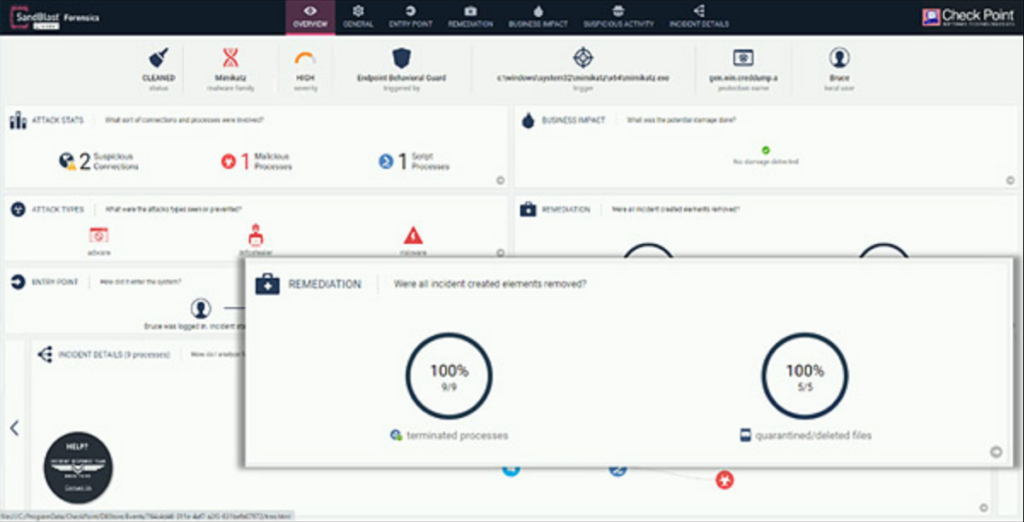
Threat Emulation uses a patented Sandboxing Technology to detect 0-day and Advanced Persistent Threats. The Threat Extraction process can clean files by wrapping them inside a PDF file to be delivered within seconds, whilst the raw file is being emulated.
To find out more about Check Point Harmony Endpoint – Advanced, to set up a Proof of Concept or Trial, please contact us now.
Check Point Harmony Endpoint – Basic
The Basic package of Harmony Endpoint provides the same Next-Generation Anti-Malware features, as well as the Compliance and Anti-Ransomeware.
It does not include the Threat Emulation or Threat Extraction features which are available in the Advanced package.
To find out more about Check Point Harmony Endpoint – Basic, to set up a Proof of Concept or Trial, please contact us now.

Check Point Harmony Endpoint – Data Protection
To find out more about Check Point Harmony Endpoint – Advanced, to set up a Proof of Concept or Trial, please contact us now.
Check Point Harmony Endpoint Product Specification
Harmony Endpoint Packages | |
|---|---|
Packages | Data Protection – includes Full Disk Encryption and Removable Media Encryption, including Access Control and Port Protection |
Harmony Endpoint Basic – includes Anti-Malware, Anti-Ransomware, Zero-day Phishing, Advanced Threat Prevention, & Endpoint Detection and Response (EDR) | |
Harmony Endpoint Advanced – includes Harmony Endpoint Basic, plus Threat Emulation and Threat Extraction | |
Harmony Endpoint Complete – includes Harmony Endpoint Advanced, plus Data Security (Full Disk and Media Encryption) Note: Endpoint Compliance is provided with all packages | |
Operating Systems | |
Operating Systems | Windows Workstation 7, 8, and 10 |
Windows Server 2008 R2, 2012, 2012 R2, 2016, 2019 | |
MacOS Sierra 10.12.6, MacOS High Sierra 10.13.4 (Threat Emulation, Threat Extraction, Anti- Ransomware, Chrome for Mac Browser Extension) | |
Linux – Ubuntu 16.04,18.04,20.04, Debian 9.12–10.5, RHEL/CentOS 7.8 – 8.3, Oracle 7.9-8.3 (Anti-Malware, Threat Hunting) | |
Content Disarm & Reconstruction (CDR) across email and web | |
Threat Extraction | Removes exploitable content, reconstructs files to eliminate potential threats and delivers sanitized content to users in seconds |
Threat Emulation | Threat sandboxing capability to detect and block new, unknown malware and targeted attacks found in email attachments, downloaded files and URLs to files within emails |
Provides protection across widest range of file types, includes MS Office, Adobe PDF, Java, Flash, executables, and archives as well as multiple Windows OS environments | |
Uncovers threats hidden in SSL and TLS encrypted communications | |
Centralised Management | |
Cloud & On-Prem Management | Harmony Service (Hosted on Check Point cloud) |
Harmony Appliance or Virtual Appliance (Hosted on premise) | |
NGAV: Runtime Detection and Protection | |
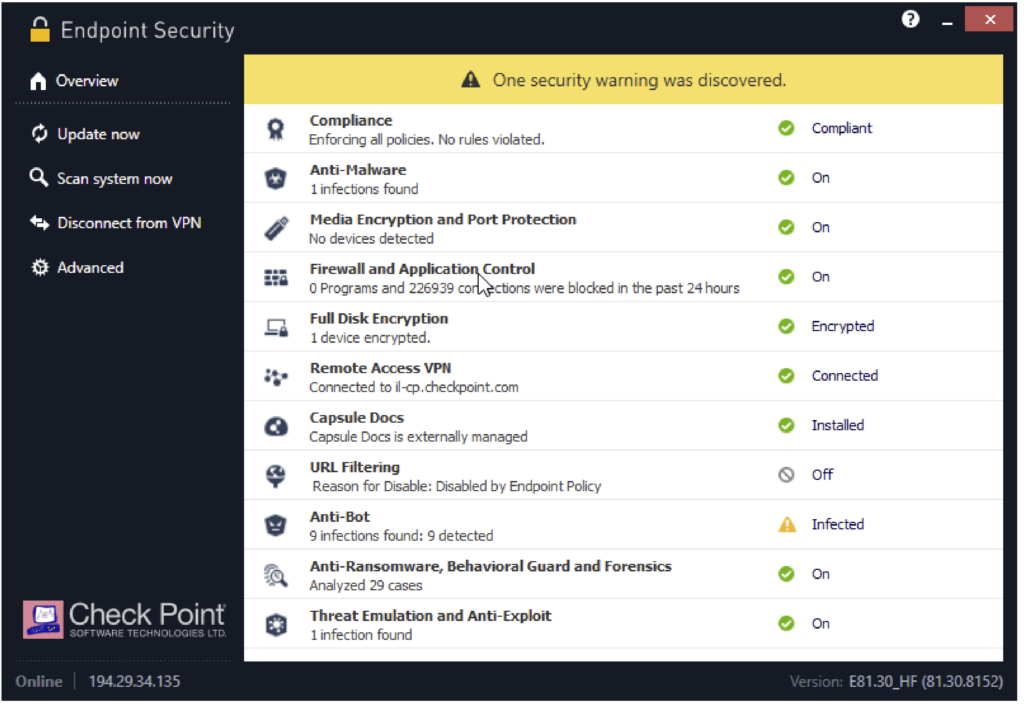
Anti-Ransomware | Threat Prevention – constantly monitors for ransomware specific behaviour and identifies illegitimate file encryption, signature less |
Detect and quarantine – All elements of a ransomware attack are identified by forensic analysis and then quarantined | |
Data Restoration – Encrypted files are automatically restored from snapshots to ensure full business continuity | |
Anti-Exploit | Provides protection against exploit based attacks compromising legitimate applications, ensuring those vulnerabilities can’t be leveraged. |
Detects exploits by identifying suspicious memory manipulations in runtime. | |
Shuts down the exploited process upon detecting one, remediates the entire attack chain | |
Behavioral Guard | Adaptively detects and blocks malware mutations according to their real-time behavior. |
Identifies, classifies and blocks malware mutations in real time based on minimal process execution tree similarities | |
Web Protection | |
Zero-Phishing | Real-time protection from unknown phishing sites |
Static and heuristic-based detection of suspicious elements across websites requesting private info | |
Corporate Credential Protection | Detection of corporate credentials reuse on external sites |
URL Filtering | Lightweight browser plugin, allow/block access to websites in real-time |
Enforce organization policy for safe internet for users on/off organization premises, enforce regulation compliance, improve organization productivity | |
Full visibility to HTTPS traffic | |
Threat Hunting | |
Threat Hunting | Collection of all raw and detected events on the endpoint, enabling advanced queries, drilldown and pivoting for proactive threat hunting and deep investigation of the incidents |
Check Point Harmony Endpoint FAQs
Harmony will work with the following operating systems
Windows Workstation 7,8 and 10
Windows Server 2008 R2, 2012, 2012 R2, 2016, 2018, 2019
MacOS Sierra 10.12, MacOS High Sierra 10.13, MacOS Mojave 10.14, MacOS Catalina 10.15, MacOS BigSur 11.x
Linux Ubuntu (16.04, 18.04, 20.04), Debian (9.12-10.10), RHEL (7.8-8.3), CentOS (7.8-8.3), Oracle (7.8-8.3), Amazon (2)
There are four Harmony Endpoint specifications: Basic, Advanced, Complete and Data Protection. Please refer to the product specification for detail on each.
Harmony Endpoint is a world-class, consolidated security solution. As you would expect, it has been lauded by industry experts. Here are just a few of these accreditations:
- Industry best catch rate and ‘Top Product’ award in the AV test review
- Rated 4.5/ 5 in reviews for Endpoint Detection and Response Solutions by Gartner peer insights
- Check Point Named ‘Worldwide major player in Modern Endpoint Security’ in the 2021 IDC MarketScape for Enterprises and SMBs
- NSS ‘Recommended’ status in AEP test
- AA product rating in the NSS Labs Advanced Endpoint Protection Test
- Check Point recognised as Leader in Endpoint Security by Forrester Wave





