Check Point Harmony Mobile is a complete Cyber Security solution for mobile devices. It is a market-leading Mobile Threat Defense solution, keeping corporate data safe by securing employees’ mobile devices from multiple attack vectors; apps, network and operating system.
App Protection
Harmony Mobile prevents malware from infecting employee mobile devices by detecting and blocking malicious apps.
Part of the Check Point Threat Cloud, the Behavioural Risk Engine runs applications in a cloud-based environment to establish if an app is malicious. The Behavioural Risk Engine uses techniques such as AI/ML, sandboxing, advanced static code flow analysis, anomaly detection and application reputation.
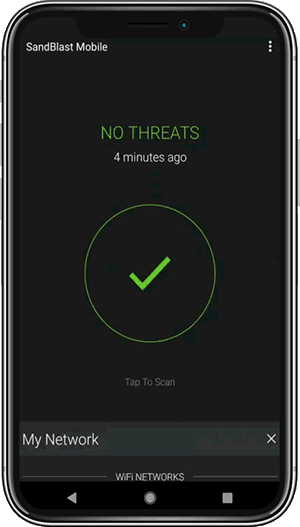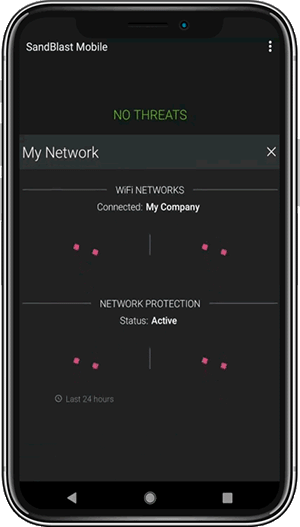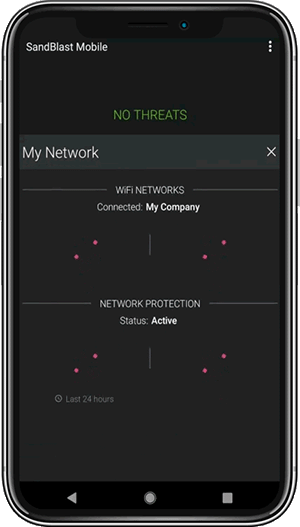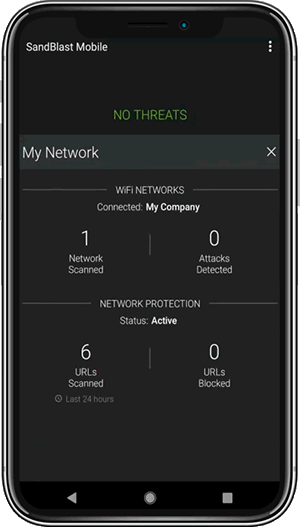
Network Protection
Harmony Mobile’s “On-device Network Protection” allows for security at the network layer of the mobile device. This brings the suite of Check Point’s industry-leading network security technologies and techniques to mobile devices.
- Wi-Fi Network Security – detects malicious or suspicious network behaviour such as Man-in-the-Middle attacks and disables connections to malicious networks.
- URL Filtering – allow or block websites that can be accessed on any browser on the mobile device.
- Protected DNS – manage and control a device’s DNS preferences to ensure privacy and help protect against malware and scamming attacks
- Anti-Phishing (incorporating Zero-Phishing) – Block phishing attacks across all applications and browsers, including sites or apps which use SSL
- Safe Browsing – Leverage the Check Point ThreatCloud to categorise website traffic from any web browser installed on the device.
- Anti-Bot – detect botnet-infested devices and block the communication to the botnet command and control systems
Operating System Protection
Ensuring devices and their operating systems are not a point of entry by detecting vulnerabilities, enforcing security controls and completing real-time risk assessments to detect attacks and advanced threats that may involve rooting or jailbreaking.

Leading Integrations
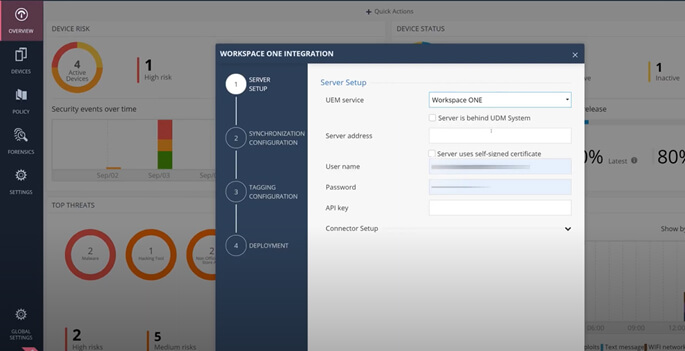
The Harmony Mobile solution integrates with any mobile management (MDM/UEM) solution such as Microsoft Intune, MobileIron, Jamf, VMware Workspace1, IBM MaaS30*, BlackBerry UEM* to facilitate a zero-touch deployment, leveraging the native ability of a MDM/UEM to facilitate the installation.
* – iOS only
Harmony Mobile works with whatever style of mobile device management is in use within your organisation:
- Bring your own device (BYOD)
- Company-0wned, business only (COBO)
- Company-owned, personally enabled (COPE)
Harmony Mobile is supported in iOS and Android, and within the Android Enterprise eco-system enables use of Work and Personal Profiles.
Simple, Integrated Management
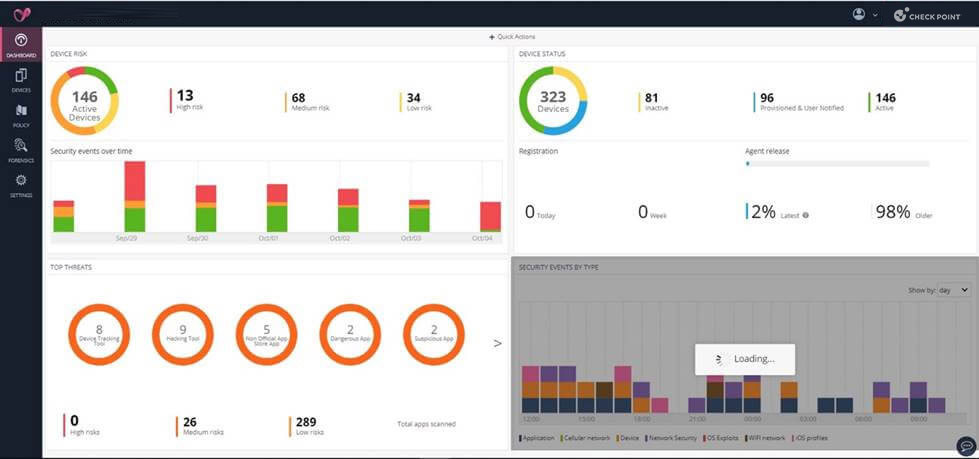
The Check Point Harmony Mobile system is managed within the Check Point Infinity Portal, the central place of management for all Check Point software solutions.
The Infinity Portal is a cloud-based intuitive management system, bringing the ability to oversee mobile risk and posture. Integrations into well-known SIEM tools for log export allows for the centralisation of all cyber security event information.
Check Point Harmony Mobile License options
The Check Point Harmony Mobile platform can be licensed in two primary ways, depending on how your organisation works.
- One license per mobile device
- One license per user, allowing each user to have a maximum of up to 3 mobile devices
There are also license options which incorporate all elements of the Check Point Harmony solution, including Mobile, Endpoint and Email & Collaboration.
Check Point Harmony Mobile FAQs
Check Point Harmony Mobile supports:
iOS: 10.x, 11.x, 12.x, 13.x, 14.x and 15.x
Android: 5.x, 6.x, 7.x, 8.x, 9.x, 10.x, 11.x and 12.x
The license of Check Point Harmony Mobile can be completed on a “per device” basis, or on a “per user” basis where a user is allowed upto 3 devices.
Check Point Harmony Mobile has won a number of industry awards and accreditations, including;
- Recognised as a Leader in the Worldwide Mobile Threat Management (MTM) Software 2020 Vendor Assessment by the ICE MarketScape, for the third consecutive year
- Harmony Mobile achieves Highest Award in Miercom Mobile Threat Defense Comparison
- Harmony Mobile featured on the 2021 CRN Mobile 100 list
Want to know more?
Get in touch today to find out more. Leave your name, number and email address alongside your enquiry, and one of our dedicated Business Development Managers will be in touch as soon as possible to answer any of your questions.
Your data will be handled in accordance with our Privacy Notice





