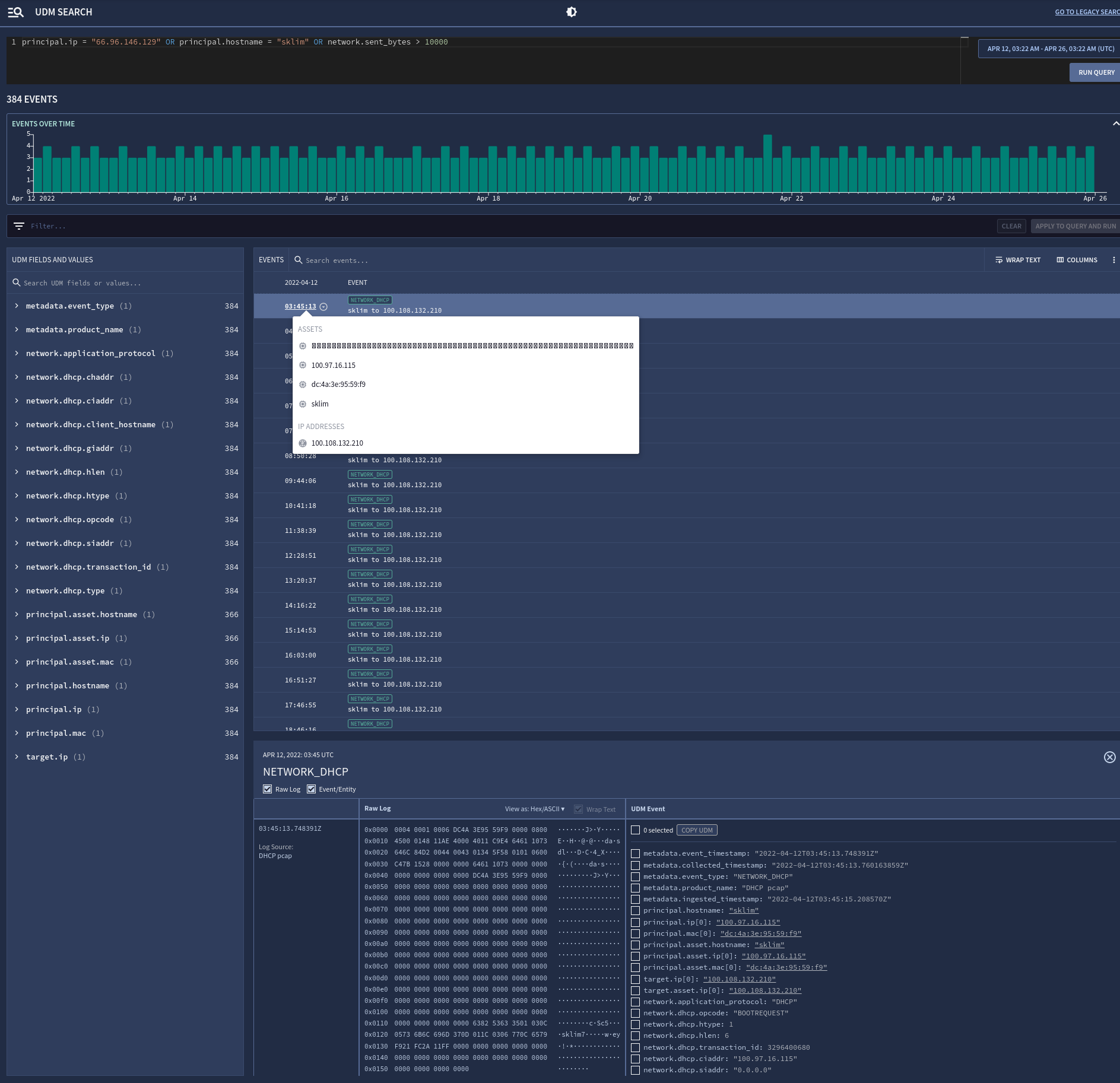
Chronicle SIEM
Security Operations at the Speed and Scale of Google
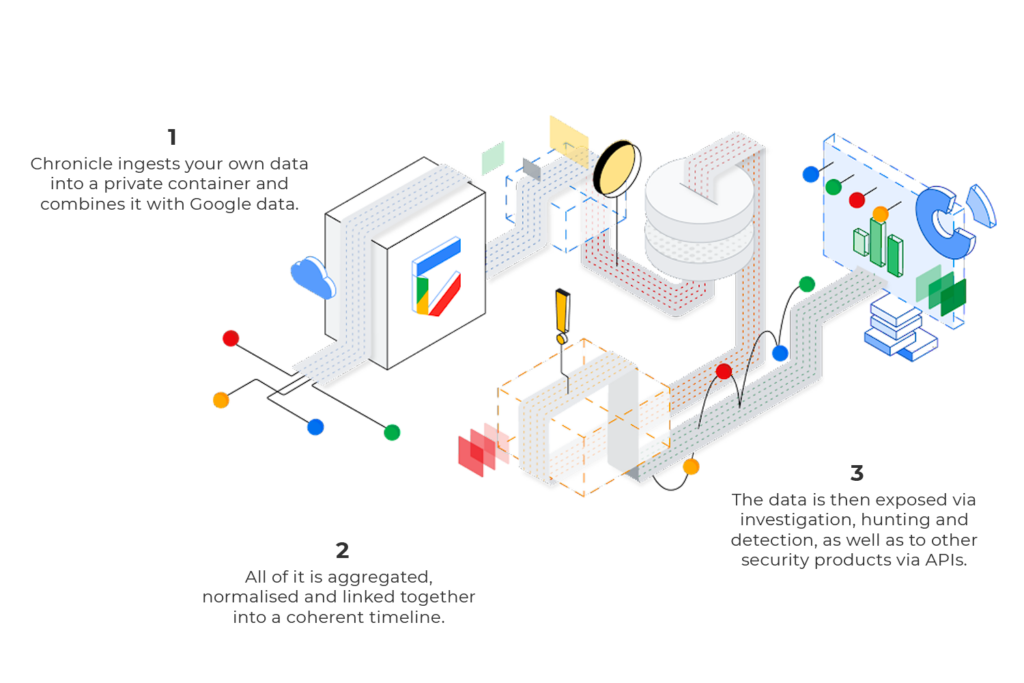
Running as part of Google’s core infrastructure, Chronicle SIEM is a cloud-native SIEM, capable of processing massive amounts of data. Supporting datasets up to petabytes in scale, logging capacity no longer becomes a consideration in your security infrastructure.
Modern Threat Detection
Purpose-Built TTP Detection Engine
Unparalleled Google Cloud Threat Intelligence driving context and insights on threat actors
Google’s out-of-the-box detection content surfacing threats faster, and identifying anomalies sooner.
Simplified detection authoring with do-it-yourself detection engineering platform, powered by YARA-L
Drive risk-based alerting and prioritization for your environment with context-aware detections
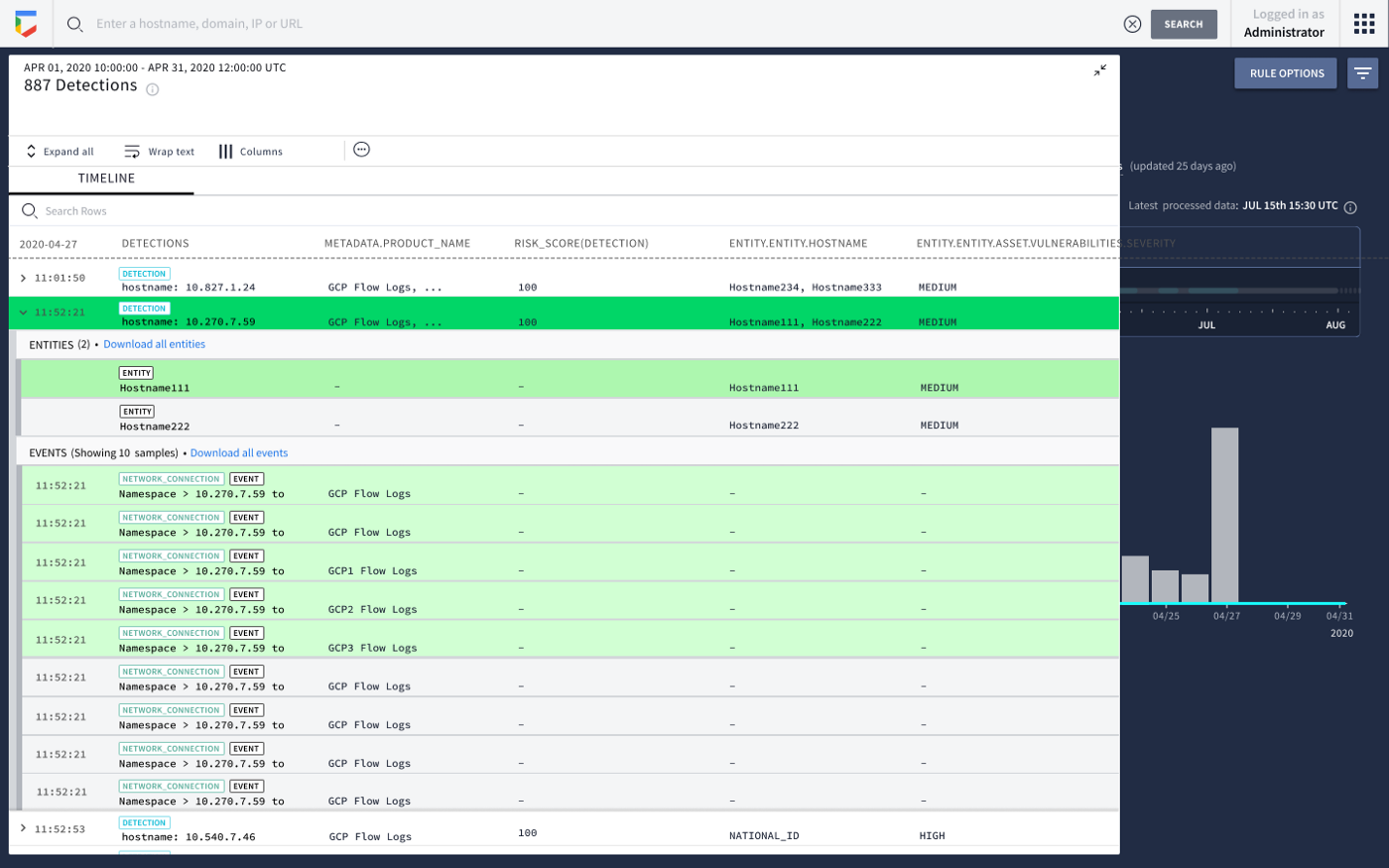
Superior Investigation
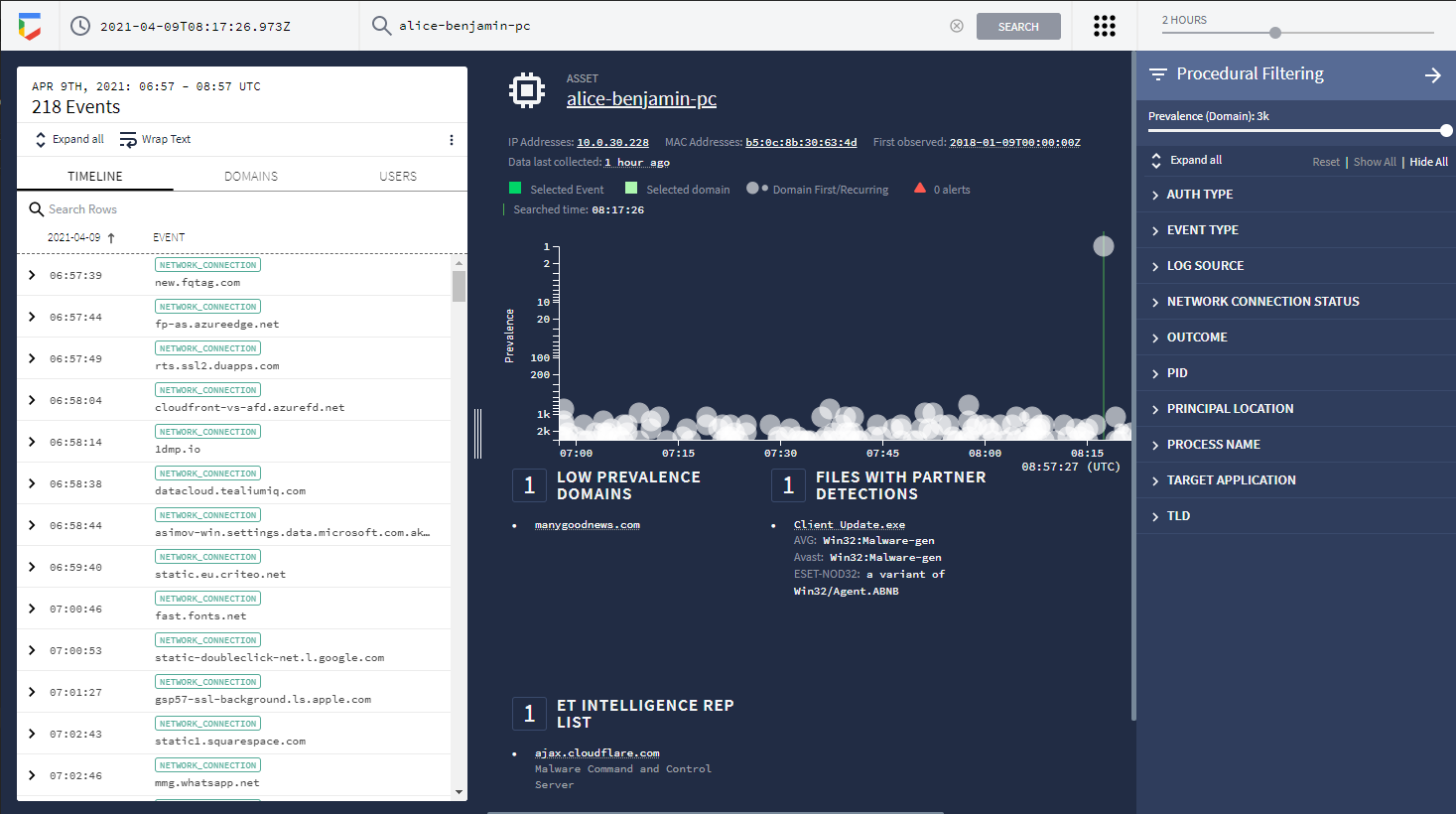
Curated investigation views drive accelerated investigative outcomes including VirusTotal enrichment, prevalence data, 3rd-party threat intelligence insights and user aliasing
Easily find anomalistic assets and domains in with prevalence visualization. Enables analyst prioritization during an investigation
Intelligent Data Fusion
Rich, extensible unified Data Model spanning Asset, User and IoC dimensions and attributes Automated IP to host correlation enables instant asset and IoC analytics
Canonical event deduplication enables simplified and quick analysis with logical event layer (user logins, network connections etc.) and visualization
Disruptive Data Retention
1 year of built-in retention of security telemetry in hot state at no additional cost.
No infrastructure procurement, deployment or tuning costs.
Enhance ROI on other security investments like EDR, enabling high-volume data sources to be retained for a full year.
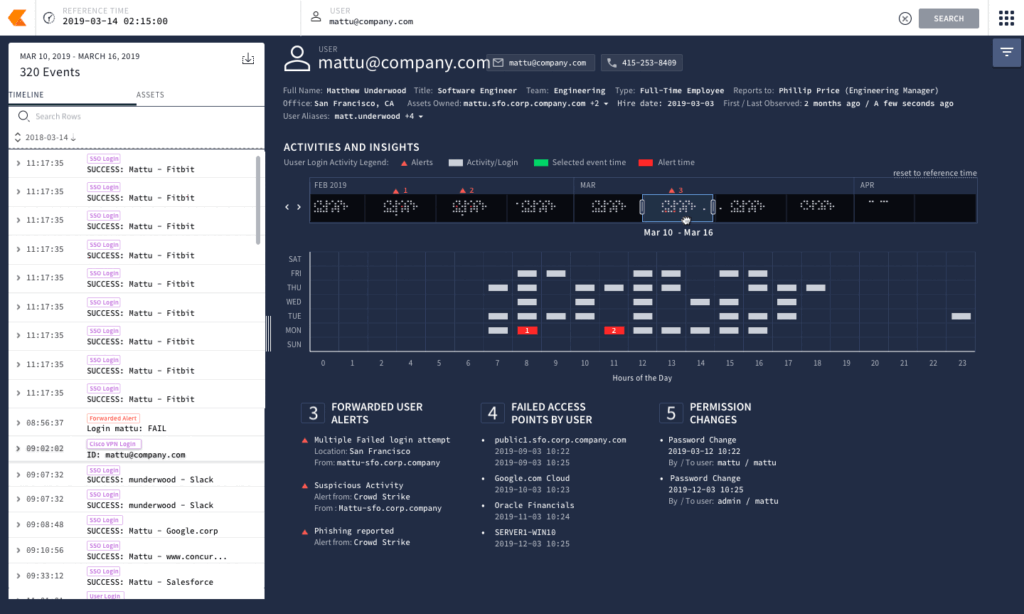
Security Analytics at Scale
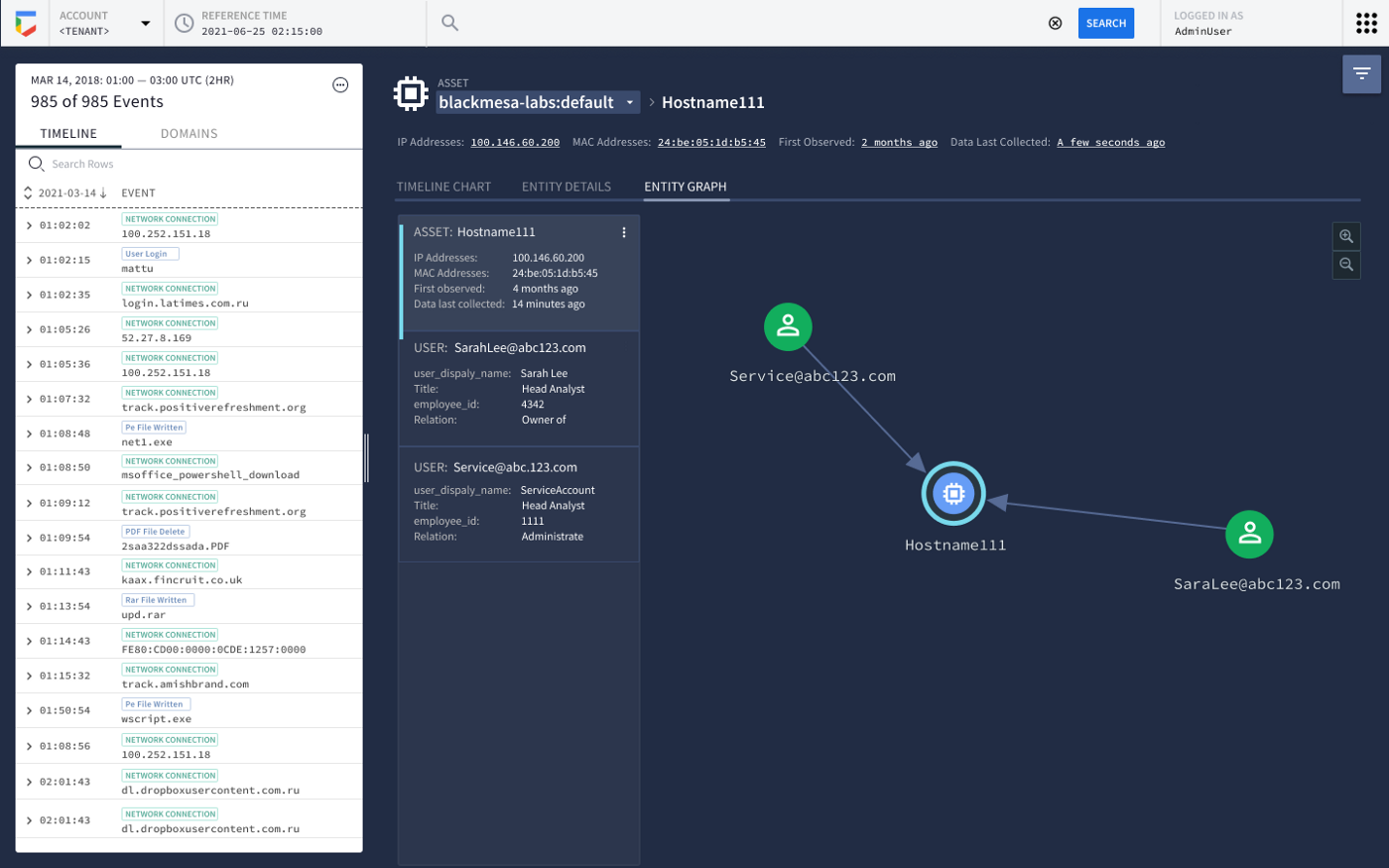
Chronicle SIEM automatically makes the connections between user and machine identity information that would normally take a skilled analyst hours to complete. Once these connections are made, they are combined into an alert for human response.
When an analyst receives an alert for a machine or person, Chronicle SIEM can instantly display every bit of related activity—no need to search through different log systems at different times to try to connect activity to an employee’s actions.
Network packets identified with an IP address connect to email logs with an email address to file transfers from a MAC address. Chronicle SIEM understands how to link these different pieces to a single asset or user.