The web browser is the single most used application by enterprises worldwide. It’s also the most-common entry point for malware and threat actors. In response, security teams are forced to surround it with a security ecosystem to protect end users, applications, and data, creating layers of complexity and leaving end-users with a frustrating experience.
Island, the Enterprise Browser, gives organisations complete control, visibility, and governance over the last mile, using the same smooth Chromium-based browser experience users expect. Access and security policies are embedded directly within the browser, where users, applications and data intersect. Now, work flows freely while remaining fundamentally secure.
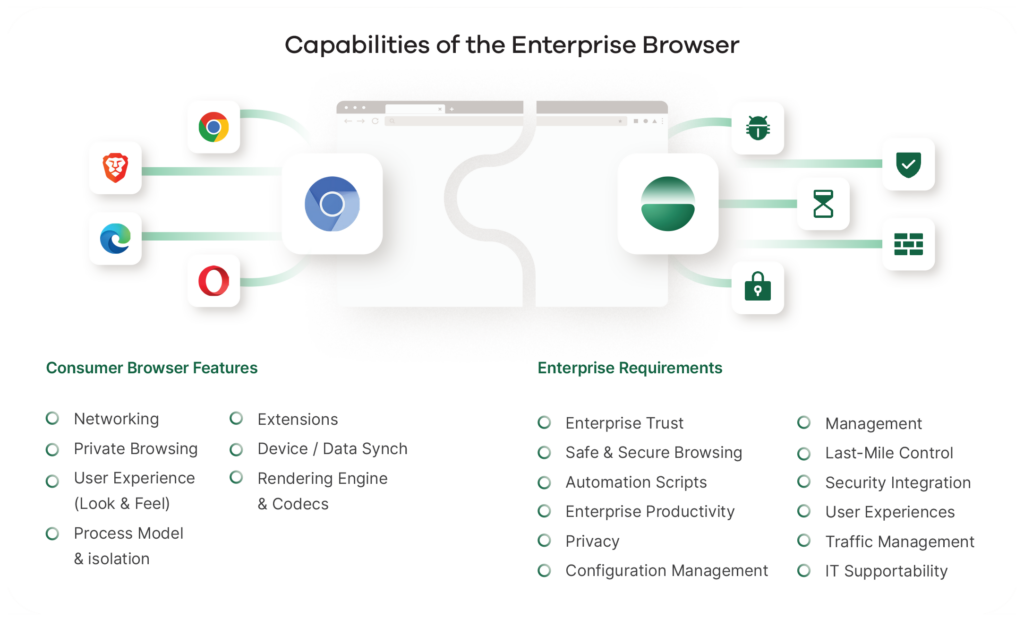
Feature Requirements of an Enterprise Browser
Last Mile Control
The ability to control and govern data is more difficult than ever now that most applications leverage SSL to hide traffic and cloud applications hold such valuable corporate data. Further complicating matters, the use of consumer browsers to access these applications creates a significant risk of data loss. These browsers allow even the simplest of actions such as cut, copy, paste, screenshots, uploads, downloads, and printing of critical data with zero governance.
The Island Enterprise Browser restores complete visibility and ensures deep control of such actions, allowing enterprise policies to be applied based on specific application needs. By establishing trust through a combination of the user’s identity and the posture of the device being used, Island can apply the appropriate policy ensuring full control over how users interact with corporate data at the critical last mile within the browser. The Island Enterprise Browser empowers IT and security teams to be very precise in controlling application usage and protecting critical data unlike ever before.
Deep Forensic Audit
Until now organisations have been quite limited in what they could see and record over user web application activities, making things like intelligence, forensics and compliance efforts difficult or even impossible.
The Island Enterprise Browser provides a complete forensic audit record of all activities with granular control over the depth of what is captured by user, device-type, application and location. Island even captures events and insights as granular as copy/paste, screen captures, printing, saving and custom information, which can be easily viewed as built-in dashboards, reports, or exported to your current aggregation platform. And where data protection and privacy concerns are needed, Island can anonymise all data to help you meet these requirements. Forensic audit logging within Island presents an entirely new dimension of information security telemetry to enrich your existing efforts.
Browser-based Robotic Process Automation
Often organisations have unique security needs that application providers or security services just can’t meet. The ability to customise a SaaS application is limited by the inflexibility of the provider and internal web applications cannot always be easily changed without convening a large team of developers.
Island provides you with the ability to insert Browser-based RPA (Robotic Process Automation) modules into the presentation layer of the browser itself, allowing for the easy transformation of a workflow within a SaaS or internal web application. As unique business needs arise, this gives you enhanced security capabilities over critical content or new workflows within an application that are specific to your organisation. For example, you might wish to redact a credit card number, auto populate fields from a corporate dictionary, insert two-factor authentication to a legacy application, govern time for hourly contractors or restrict the time an end user can spend on a particular site. Your unique needs and imagination are the only boundaries.
Centralised Policy
Governance over the browser real-estate is typically very rudimentary at best. Usually, such policies over this real-estate are rudimentary functioning on binary objects within the consumer browser configuration. Island delivers centralised management over your Enterprise Browser real-estate with extensive capabilities to safely protect all critical application usage at a deep and flexible level. Island allows you to gain deep control by integrating into identity management, leverage device posture for decisions, manage security over any SaaS or internal web application, and create new dimensions of logging outputs. Governing the browser footprint centrally, ensures that the browser can be a powerful part of the organisational security architecture.
Safe Browsing
Everything from the SaaS processes you deploy to the websites your employees visit must be safeguarded. It’s harder and harder to leverage traditional approaches for such things to be effective. An increasing amount of traffic is just being passed through network inspection technologies; however, the explosive use of SSL makes network inspection exceptionally painful and even impossible in some cases.
Island delivers a new level of safe browsing and full visibility not offered by other security solutions. With built-in protection including malware inspection, site categorisation, web isolation, anti-exploitation and credential harvesting protection, the Island Enterprise Browser allows users to freely browse the Internet ensuring they are always safe.
Built on Chromium
Enterprise end users have expectations with how their interactions with the web sites and applications work. All too often, security technologies are introduced to protect organisational resources which deliver a subpar experience for the users. This results in unhappiness and cultural abandonment of the technology by the user population.
By relying on Chromium at its core, Island assures that users will always operate in the familiar and stable confines of a browser experience they’ve always known. All sites and applications will behave exactly as they have before, and Island’s built-in control and governance ensures that the organisation’s critical resources always remain protected. Users are happy and security is strengthened. Everyone wins.
Use Cases
3rd Parties / Contractors / Business Process Outsourcer
Native web access with built-in data protection, device assessment without cumbersome MDM tools.
BYOD
Quickly implement access & control to sensitive and proprietary web applications without the need to re-platform or deploy countless security agents.
VDI Augmentation / Reduction
Reduce the need for VDI environments for web access with a native browser that provides all “last-mile” protection & unmatched visibility.
Compliance
Controlling the last mile ensures that changing demands on data access do not require costly application redesign.
Critical SaaS & Web Apps
Provide monitored & protected access to critical applications ensuring a closed-loop system where data cannot escape.
Safe Browsing / Native Browser Isolation
Allow users to freely browse the Internet with native protection to prevent unknown or malicious sites from introducing risk.
Zero Trust Access
Complete your Zero Trust program with a trusted and managed browser that provides strong authentication & monitoring.
Sensitive Access (Privileged Users)
Enhanced logging, monitoring and protection when admins access web-based administration & configuration consoles.
Want to know more?
Get in touch today to find out more. Leave your name, number and email address alongside your enquiry, and one of our dedicated Business Development Managers will be in touch as soon as possible to answer any of your questions.
Your data will be handled in accordance with our Privacy Notice





